The Neighborhood Network Watch (NNW) is a simulation of a possible next step for network-based government eavesdropping operations through a community volunteer group that monitored the network traffic of public and private WiFi access points for terrorist activity. This simulation acts as vehicle to localize and engage the public into critical discussion about some often distant and or overlooked issues that affect their everyday lives. These include the embedded politics and power within everyday technology and networks, the ways in which entities that own, control, access, and exert power over networks use the data that we transfer everyday over them, and hierarchical power at large.
The group is modeled after the neighborhood watch programs, which enlists citizens to look out for the community, and the U.S. Department of Homeland Security’s (DHS) goal to “safeguard” our nation by any means necessary, legal or extralegal. The group’s history is intertwined heavily with the DHS’ own history as well as current events. They see themselves as a progressive government affiliated group that has the flexibility to adopt new emerging technologies, such as Web 2.0 for strategic purposes. Their methods and tactics are rooted in guerrilla warfare and counterinsurgency warfare, substituting arms for off the shelf electronics to carry out network eavesdropping to identify networks that maybe being used by terrorists. There primary targets are publicly accessible and publicly used wireless networks and encouraging the community to monitor their own home networks.
The Five Components of the NNW:
–Collection
–Analysis
–Web Presence
–Public Service Announcement (PSA) Series
–Performances
In addition some of the byproducts of the five components are manifested as printed materials or objects.
Collection
The collection portion of the NNW covers the methods and tactics that could and can be used to collect actual data being transferred and received across networks with everyday electronics. Many of the tactics come from Mao Tse-Tung’s, USMC Brigadier General Samuel B. Griffith’s analysis of guerrilla tactics and counterinsurgency warfare, as well as current day tactics being employed by terrorist and insurgent groups. The technology side is comprised of everyday WiFi enabled devices, primarily laptops loaded with open source packet sniffing software like TCPDUMP. In addition TCPDUMP has also been tested and run off mobile platforms such as iOS mobile devices.
Analysis
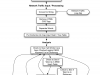
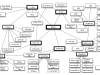
The Neighborhood Network Watch Keyword Analysis Application v3.6 (NNWKAA) is a multithreaded Java/Processing text analysis application that looks for words associated with terrorism or national security threats, within raw network dumps and assigns a rating. The NNWKAA first breaks down the raw network dumps by stripping out extraneous information, e.g. HTML and CSS tags. Next the NNWKAA looks at each word within the network dump and checks to see if it is on a list of flagged words that are known to be associated with terrorism or national security threats. This list is known as the Neighborhood Network Watch Keyword List (NNWKL). This list is based on the cold war era ECHELON word list that has been supplemented with data that has been scraped from the FBI and INTERPOL websites. If a word is flagged the application pulls the word preceding and following the flagged word. These words become contextual words that maybe eventually added into a separate word list, which acts as a supplement to the NNWKL, to allow the applications word lists to learn over time and automatically expand or initiate mission creep. If a word is not flagged it is cross referenced with the WordNet Lexical database to ensure the word is a word. From here the application then calculates the “Terror Percentage” which is the amount of words flagged to the total number of words found. Also, outputted are the counts for both flagged words and the total number of words. Based off of this percentage the application also generates a rating for the network traffic using a rating system that is similar to that of the Department of Homeland Security, both in verbiage as well as in description. Along with this rating a listing of the top 20 flagged words, also known as the hit parade, is then generated and displayed. At this point the contextual words that were found around the flagged words have probabilities calculated for them to see if they meet the minimum requirement to be added to the supplementary word list. In addition there is a minimum occurrence threshold as well. These words are then added to the supplementary word list and the statistical results and the hit parade are outputted to text files. A flow diagram of the NNWKAA can be viewed here.
The NNWKAA is not meant to be an accurate tool for finding terrorist, rather it is designed to inflate the amount of perceived terror that is found in the network traffic dumps. This amplification of terror acts as both the fuel and pretense for the ideology that governs the NNW. It also is able to demonstrate that software, systems, and apparatuses are not necessarily objective entities that are infallible. Rather they are subjective and are governed by the entities that designed them and in turn often reproduce the ideologies of those creating any given application. The NNWKAA also critiques and foregrounds the usage of opaque systems such as the DHS’ five-tier color coded Homeland Security Advisory System.
Web Presence
The NNW’s web presence contains its history, its fictitious results, news on the group’s activities, upcoming events, policy and future plans, all of which operate as subtle propaganda. The site is a sprawling 120+ page site modeled after the DHS’ own site. In addition there is NNW Web 2.0 and social networking presence on sites such as Facebook and MySpace that serve as a means for communication and coordination, as well as YouTube and Google Video for their PSA series. You can still visit the original NNW website at www.dhsnnw.org.
Public Service Announcements
The NNW’s public service announcement series operates as video based propaganda and documentation for the fictitious group. The public service announcements are typically short videos ranging from two to six minutes in length that discuss a number of topics. Some aim to present the fictitious history and findings of the group while others offer documentation of events attended by the NNW, known as “special presentations.” They are narrated by myself and often incorporate me as a high-ranking official for the NNW. The tone of the PSA’s are typically benign and friendly despite some of the outlandish claims and statements made during them. They have been primarily viewed within web contexts, those being the NNW official website, YouTube and Google Video. They are also sometimes seen alongside the performances and operate like props. In total there are currently seven released public service announcements.
The Neighborhood Network Watch: Introduction (PSA #1)
The Neighborhood Network Watch: ITP Winter Show 07′ (PSA #2)
Performances
The NNW public presentations/performances bring together all the varying components of the project and are presented in two different formats. The two presentation formats are PowerPoint podium style presentations and trade show recruitment style booth setups. With these presentations I make usage of many of the other components that comprise the group as props and artifacts. Throughout this process individuals who interact with me and or the project will often begin to raise questions, start a dialogue and deconstruct the simulation. During the ensuing dialogue we can discuss how these issues have a direct relationship to them while also raising awareness of current events, past historical context, and a deeper understanding of networks and technologies utilized in their everyday lives.
Exhibitions, Performances, & Talks
NNWKAA: Making Terrorism Out Of Your Emails, 18th Street Art Center, Santa Monica, CA
Have You Seen My Privacy, 18th Street Art Center, Santa Monica, CA
Collective Show LA, 995 N. Hill Street, Los Angeles, CA
Electrofringe: 2010, Project Space, Newcastle, New South Wales, Australia
A Day in LA: Washington Blvd Art Concert, Whittier, CA
OURS Democracy in the Age of Branding, The Sheila C. Johnson Design Center / Vera List Center for Art and Politics, Parsons The New School for Design, New York, NY
ITP Spring Show 2008, New York University, New York, NY
Sousveillance Culture Conference, The Change You Want To See Gallery, Brooklyn, NY
ITP Winter Show 2007, New York University, New York, NY
Electronic Social Club, Hunter College, New York, NY
During the project the website has had over 50,000 viewers with over 500 referring sites, most of which are blogs with their own interpretations and takes on the project. The public performances have been great successes with people taking the time to talk and discuss at length about the various issues raised by The Neighborhood Network Watch.
Selected Press
The Register: “Unmasking the Neighborhood Network Watch”




















One Trackback
By The Neighborhood Network Watch @ 2008 ITP Spring Show | Emery C. Martin 3 Mar ’14 at 5:51 pm